Powered by Arctic Wolf
"Securing Your Business and Customer's Information"
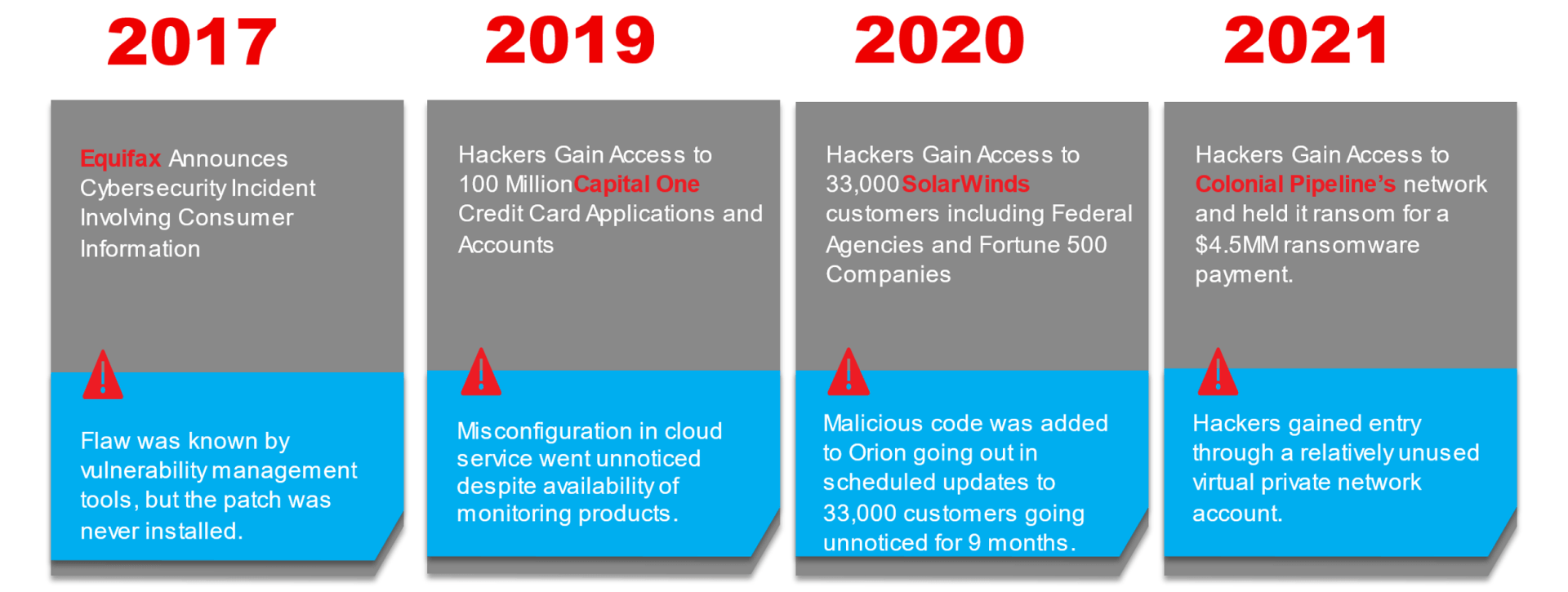
It is not a matter of "IF"...
It is a matter of "WHEN"...
Security Operation Center As A Service
Cyber Security Specialists
TLN is a Registered and Authorized Business Partner with Lenovo, certified for PC and server repair and deployment. Our services are backed by Lenovo and all parts are OEM, handled by experienced computer network engineers.
Lenovo is a global leader in IT, esports and VR products. Since 2010, our roots have been in technology and competitive esports. The cross-section of esports and education is a focus we continue to develop and expand our offerings with an incredible partner like Lenovo.
TLN offers complimentary initial consultations to those considering system deployment or data migration. You’ll explain your technology strategy and what your current system lacks (if applicable) to our experienced Lenovo technicians, who will strategize how our services can help.
ANALYSIS
Our certified computer network engineers evaluate your current network infrastructure and hardware to determine what will be needed to achieve results. From there, the quantities and requirement details of your solution will be taken to our authorized design engineers for preparation.
DESIGN
System designers at TLN are trained to obtain appropriate, compatible equipment and licenses. You will receive a quote within 24-48 hours and an estimated timeframe for arrival and completion. We are partners and certified with Lenovo, so you can be confident that your IT solution will meet expectations and supported by both TLN and Lenovo.
IMPLEMENTT
System deployment is a two-step implementation:
1. Off-site configuration. Our system engineers assemble and program your Lenovo hardware to specification.
2. On-site deployment. Computer network engineers convert and setup your new Lenovo system, along with experienced cabling technicians if necessary. We can safely remove and properly recycle unneeded hardware, securely erasing any of your existing data.
SUPPORT
TLN is committed to your success and happy to offer comprehensive support services after deployment. From user training to future changes and alterations, there may be little bits and pieces that you realize afterwards that need adjusting or explaining – and we will gladly assist you.
Free Consultations
24/7 Monitoring
Turnkey Concierge
Hours:
Now Offering
Virtual Consultations
Submit your request today to set up a live video consultation with The LAN Network from your smartphone, tablet, or computer!
Get Better Security Effectiveness for Your Organization
The LAN Network is a cyber security company providing Security Operations Center as a Service, or SOCaaS, to clients in multiple industries who are concerned with mitigating business and reputation risk, staying competitive, protecting revenue, and are stretched thin. SOC-as-a-service is a subscription-based, outsourced alternative to an in-house security operations center (SOC).
Security Operations Center as a Service is our main differentiator and key selling point. As a SOC-as-a-service vendor, we offer a comprehensive set of solutions, such as managed detection and response, and provide organizations with a dedicated team of experts who are available around the clock to detect, monitor, and respond to incidents. SOC-as-a-service combines people, processes, and technology to deliver cost-effective cyber security and help organizations maintain compliance.
Our platform collects and enriches endpoint, network, and cloud telemetry, and then analyzes it with multiple detection engines. Machine learning and custom detection rules then deliver personalized protection for your organization. While other products have limited visibility, the vendor-neutral platform enables broad visibility and works seamlessly with existing technology stacks, making it easy to adopt while eliminating blind spots and vendor lock-in. Call us today to request a demo of our services.
"Many security teams have overinvested in a plethora of tools. As a result, they are also suffering from alert fatigue and multiple console complexity and facing the challenges in recruiting and retaining security operations analysts with the right set of skills and expertise to effectively use all those tools."
- Gartner
Cyber Security Has an Effectiveness Problem
3,000+
Vendors in the Industry
$120B
Spent on Cyber Security Annually
3,950
Reported Breaches in 2019
Security Operations Is the Solution
Cyber Security is a field that requires 24/7 vigilance and constant adaptation. Our cloud-native platform and Concierge Security Team delivers uniquely effective solutions.



Share On: